Introduction
The company Worldwide Advertising, Inc has two sites in Houston, TX and Richmond, VA. Various departments are spread across these sites. Networking equipment is already in place for both sites, which are separate Active Directory Domains. In addition, some departments shall want their data to remain private from other departments while security mechanisms would remain separate. Windows Server 2012 is used in the proposal.
Active Directory Infrastructure
Features for integrating the newly acquired company’s domain into their existing forest
PowerShell feature will be used for integrating the new domain into the existing forest. An additional Active Directory will need a single Windows PowerShell with the name of the domain of Worldwide Advertising, Inc., as the main domain name. Windows PowerShell will be critical because of the distributed computing. It would allow one engine for the system configuration and maintenance. It shall enable fully featured scripting of any additional elements and allow remote administration of servers.
Forest Functional Levels implementation
Forest functional levels will be implemented in phases because the AD DS supports this approach. There would be multiple functional levels with Windows Server 2012 OS. These different levels will offer configuration advantages for the AD DS elements and ensure compatibility with the entire system.
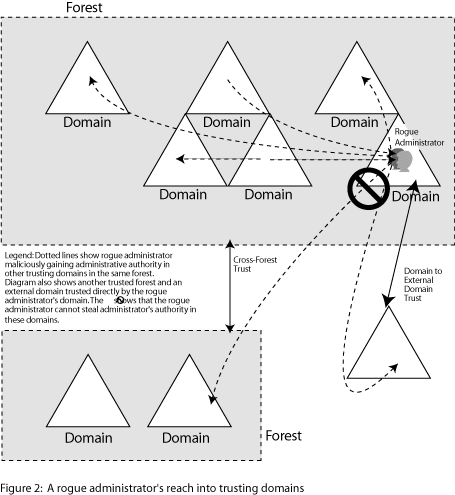
Cross-forest trusts implementation
Cross-forest trusts will be implemented to maintain connectivity between users and the main domain (Smith, 2005). The AD DS will store data for system objects on the network and ensure that data are available to users and administrators as specified. Cross-forest trust will extend the reach of AD infrastructures to other forests and the second domain in the company.
Different forests will provide adequate separation of administrative authorities and protect data across departments.
Replication
The PowerShell for Active Directory will manage replication. Replication will manage potential failures. Implementation would ensure that all changes at the main server are replicated in the secondary server (Active Directory Replication on Windows Server 2012, n.d).
Read-Only Domain Controllers
RODCs shall provide alternative to other writable domain controllers. RODCs will support roles of domain controllers without necessarily exposing AD DS applications to several system risks. Users, however, will not be able to alter the domain database on the RODC. The AD DS database on the RODC shall not allow any modification requests from other applications and users. Users will send their requests to a single writable domain controller. Replication of the Active Directory changes will only take place through a writable domain controller in a single way.
File and Storage Solutions
BranchCache
WAI will use BrachCache to optimize WAN bandwidth when employees from other branches access contents on remote servers. This application shall support copying and caching of contents at the branch office locations. Hence, users will gain access to contents locally rather than over the WAN.
BranchCache would increase employees’ productivity by enhancing content search response time for clients and servers in the office. In addition, it will also enhance network performance by lessening traffic over WAN.
Users will protect BranchCache from potential network threats and information disclosure.
Dynamic Access Control
Dynamic Access Control shall help WAI on data governance by restricting information access and audit users who accessed data. It would allow the company to identify data through applying automatic and manual classification modes, for example, by tagging file servers in all departments. Dynamic Access Control shall apply safety-net policies that rely on central access policies and define users who can gain access to financial records, Accounts and Sales Department and Creative, Media and Production Department data. The central audit policies would ensure compliance reporting and forensic analysis, for instance, the company shall be able to identify users who gain access to specific files. The Rights Management Services (RMS) will offer file encryption for all sensitive Microsoft Office files (Dynamic Access Control: Scenario Overview, 2014).
Storage optimization
Storage systems will be optimized through tiered storage spaces to improve storage performance (Otey, 2012).
Disaster Recovery
Windows Server Backup
WAI will use the Windows Server Backup to back up preferred volumes, system and files. It would be used to create a backup for quick recovery. This application shall ensure the system administrator can recover volumes, files, system applications and the system prior state after a disaster. In addition, it will aid bare metal recovery in case of hard disk failure. The system volume or server would be used for backup recovery.
In addition, Windows Server Backup will be deployed to create and management backup for both local and remote computers on the network. The backup will be scheduled to run automatically for all systems in the organization.
Volume Shadow Copies
The VSS will be used for developing shadow copies or a point in time image for selected servers or volumes. The images will offer platform and folder system consistency. In addition, it would be used for other purposes such as backup, system restore and data mining among others.
DNS and DHCP
DHCP installation and authorization
WAI install DHCP for automatic distribution of critical “IP configuration settings to network clients, eliminating the tedious and burdensome task of manually configuring hosts on TCP/IP-based networks” (Lanz, 2013). In addition, DHCP shall provide “configuration information and interact with other networking services such as domain name system (DNS), windows deployment services (Windows DS) and network access protection (NAP)” (Lanz, 2013).
No DHCP servers will service any client before they are authorized for the company network. Therefore, DHCP servers shall be registered in the Active Directory system for client servicing.
DHCP scope design
Lease time will be changed to 10 days because of the large number of IP addresses available for employees’ workstations. Increased lease time shall reduce cases of lease renewal queries. As such, there would be reduced network traffic originating from renewal requests.
The fastest client transaction rate of at least 500/sec will be considered when defining the number of scopes of the DHCP. The address range will include 192.168.1.1 to 192.168.1.100. Additional ten addresses could be included to support portable devices while specific range would be defined for such devices.
A form of DHCP fault tolerance
A form of system fault tolerance will be used by dividing the DHCP scopes. The scopes shall be split between the two servers at the ratio of 20:80 for optimum benefit. This ratio would allow servers to handle DHCP traffic flood faster. Moreover, any failure in the servers may not affect the entire network.
DHCP reservations
DHCP reservations will be used for servers to define IP addresses for various access devices (desktops, laptops and mobile) available in the company while all IP address processes will be defined at the scope level.
DNS namespace design shall be defined before the deployment of the DNS system. Internal namespace is recommended for the company so that it only remains accessible to employees within the internal network. An administrator shall maintain and manage all other functions.
The DHCP and DNS infrastructures would be integrated to allow for system updates, particularly for additional or new devices or when IP addresses of devices change on the network. WAI will have split DNS for Internet/intranet to eliminate administration burdens and system complexity involved in host configuration. DHCP Server service would offer alternative automatic configuration.
IPAM utilization
WAI is most likely to face challenges associated with the management of IP addresses because of its numerous divisions and employees. The company will use IPAM for the following purposes. First, WAI will use IPAM for network planning by eliminating manual tools and scripts that consumer much time, lead to inconsistency and other additional expenses during expansion, introduction of new technology or system upgrades. Second, the company will use IPAM to manage all IP addresses on the network through a single platform. It would be suitable for optimized use and capacity management for DHCP and DNS services with the distributed network environment of the company. Third, IPAM shall help in tracking and forecasting usages of IP address, particularly in areas with limited supply. Finally, IPAM will ensure that WAI complies with the regulation requirements e.g., for auditing purposes.
IPv6 utilization
For better Internet connectivity and efficiency, WAI will use IPv6 to cater for the shortcomings of IPv4. It would offer scalability for future Internet needs (Howie, 2013).
DNS implementation
DNS server will be configured to support other systems running on older OSs. In addition, the network administrator will monitor and manage DNS servers from a central location. Information gathered from DNS server will support IPAM (Lanz, 2014).
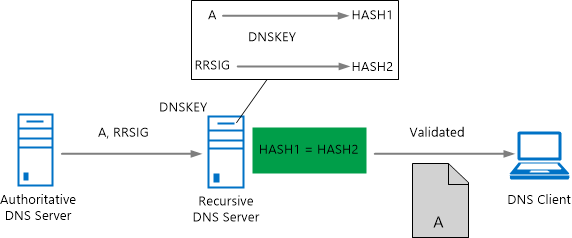
DNS Security
The DNS will rely on Domain Name System Security Extensions (DNSSEC) for security. It would ensure that all responses are validated on origin authority, data integrity and authenticated denial of existence. DNSSEC shall reduce cases of spoofing attacks on the network.
DNS for the second site
The second site will have DNS service for user login to reduce traffic directed to the VPN. Configuration shall allow users to gain access to the DNS Server, which would serve as the main DNS.
High Availability
Hyper-V
Hyper-V virtualization will offer several benefits to WAI. The feature will enhance replication to virtual machines across Data Center, Clusters and storage systems. Its Storage Migration would allow users to migrate virtual hard disk to another physical location while the machine is in motion while storage on SMB2 file shares will now support SMB2 file sharing in virtual machine storage systems. Finally, the Virtual Machine Snapshots shall allow users to delete a snapshot and create more space without shutting down the machine.
Network Load Balancing
WAI may deploy NLB to manage two servers as a single virtual cluster. NLB will improve availability and scalability of the Internet server platforms deployed on the Web. These may include mission-critical servers, firewall and other proxy elements.
Failover Clustering
This application will allow the company to have improved availability and scalability of its server workloads. Specifically, it would ensure availability and scalability of Hyper-V, SQL Server and file servers. Applications may use physical or virtual machines.
Active Directory Certificate Services
AD Certificate Services used in both domains
WAI can deploy AD CS on both servers, including Windows Server 2003. However, the network administrator must understand that not all OSs may support all components or design specifications. Hence, this application shall require testing before deployment in the company’s production environment.
The company may also wish to deploy AD CS on a single server with one certificate authority.
Active Directory Rights Management Services
Use of AD Rights Management Services
The company will use AD RMS for security purposes, specifically for encryption, authentication and certificate protection to help in developing a reliable data protection system.
AD RMS will be deployed to enhance security strategies for WAI by protecting files, enforcing personal preferences on transmitted files and enforcing organizational policies on confidential information.
Information rights management (IRM) found in AD RMS application will ensure the following outcomes. First, it would enable persistence usage policies irrespective of file transfers. Second, additional layer shall ensure information privacy for finance, creative, human resource and other departments that require data protection. Third, it shall protect contents from unauthorized recipients. That is, an authorized user may not copy, send, modify, forward, print, fax, or paste such contents for unauthorized purposes. Fourth, it would prevent unauthorized printing from the screen menu. Fifth, the feature shall support file validity period to restrict viewing after the specified period has expired. Finally, it will enforce corporate policies on information safety.
However, WAI will have to account for the shortcomings of AD RMS. For example, finance department must note that AD RMS shall not protect data against theft, deletion, capture and transmission through malicious programs and other forms of spywares. It would not guard against content corruption and loss attributed to viruses. Restricted information may be hand-copied or retyped, users may take digital photographs or use third party screen capture platforms.
Active Directory Federation Services
AD Federation Services
WAI will enable these features to ensure simple, safe identity federation and sign-on advantages for end users who may wish to use AD FS-secured channels within the company’s network.
AD FS relies on a claim-based access authorization and authentication model to ensure system security. This is a simplified approach to system and application security.
Unlike prior versions, the Windows Server 2012 has additional features to support AD FS. First, the device workplace join would allow users to connect their personal devices and manage risks during network access sessions. Second, the AD FS shall ensure that WAI manages risks through multiple access control systems. The system controls access based on users’ profile and authorization levels. For instance, it accounts for user attributes, device features or request attributes and the system must verify all these attributes for authentication and access authorization. Third, the application enables risk management through multi-factor authentication specifically for sensitive platforms. Users can control policies for files that require multi-factor authentication or with regard to request specifications. In addition, the application shall provide extensibility locations for integrating further security features to ensure secure, seamless multi-factor advantage for users. Finally, AD FS shall ensure that the company has authentication and authorization capabilities to allow access to the Web platform resources from the extranet. These are platforms with protection from the Web Application Proxy.
References
Active Directory Replication on Windows Server 2012. (n.d). Web.
Dynamic Access Control: Scenario Overview. (2014). Web.
Howie, J. (2013). IPv6 Support in Windows 8 and Windows Server 2012: Avoid IPv6 problems. Web.
Lanz, W. (2013). Windows Server 2012 DHCP (Part 1). Web.
Lanz, W. (2014). Windows Server 2012 IP Address Management. Web.
Otey, M. Top 10: Windows Server 2012 Storage Enhancements. Web.
Smith, R. F. (2005). To Trust or Not to Trust: Domains and forests and the risks of trust relationships. Web.

